Hypervisors power not just the cloud but are becoming a commodity in mobile phones and desktops as well. They separate virtual machines from each other, enabling strong isolation and security guarantees. In cloud environments, hypervisors separate non-trusting virtual machines and an attacker may try to compromise and gain access to a co-located virtual machine of a competitor. In mobile environments, hypervisors may isolate between trusted applications that process highly sensitive data and untrusted environments. On desktops, hypervisors may separate recovery environments from general purpose environments. In all cases, an attacker with access to the untrusted side wants to escalate their privileges to gain access to the hypervisor which in turn has access to all other virtual machines.
Under this attacker model, we have already explored automated testing (fuzzing) by targeting virtual devices. Fuzzing is the dominant technique in software testing that uses feedback (often through coverage --- code areas that have been executed) from the execution of automatically created inputs to guide the mutation of future inputs.
When switching from the guest operating system to the hypervisors, virtual devices interpret the request and act on it. As they are implemented in software and need to parse complex requests, they are prone to bugs. During our earlier work ViDeZZo that we published at Oakland'23, we explored dependencies in requests to virtual devices with particular focus on dependencies across multiple messages and dependencies of fields inside a message. While this allowed us to discover some severe bugs, we were not completely satisfied with the achieved coverage.
Therefore, we explored ways to create an even better fuzzer for virtual devices that achieves higher coverage and finds deeply hidden bugs. In Truman at NDSS'25, our intuition is to construct detailed device behavior models that the fuzzer can use to thoroughly and precisely explore virtual devices.
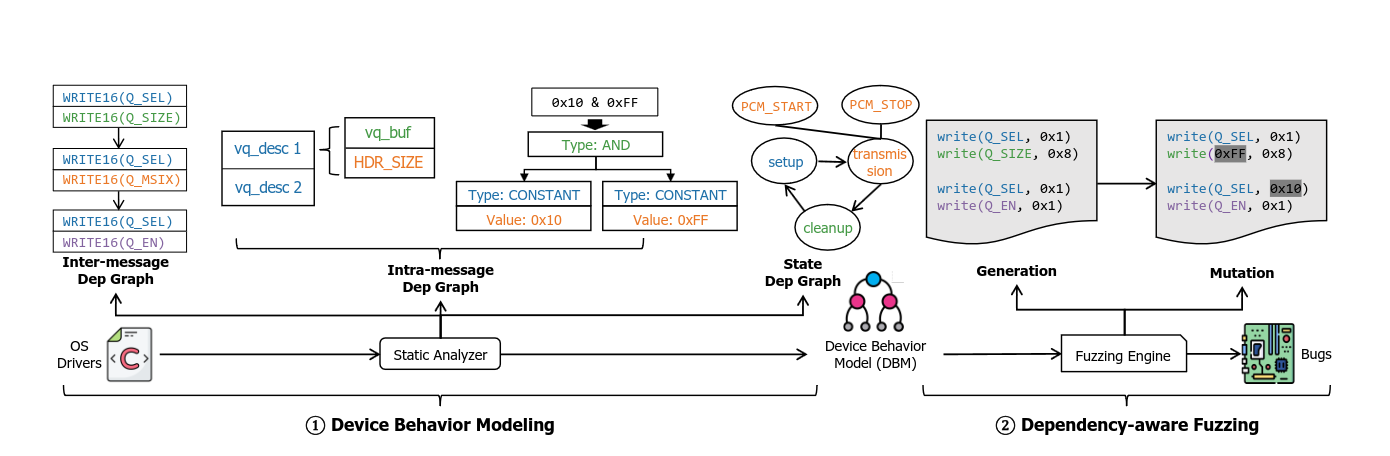
Our two core contributions are that we (i) infer state dependency and model that state of the underlying device and (ii) automatically infer three kinds of dependencies by analyzing the source code of open source virtual device implementations. The three dependencies are inter-message dependencies (similar to Truman), intra-message dependencies (again, similar to Truman) and state dependencies.
Using these extracted dependencies, our fuzzer then drives the exploration of virtual devices in QEMU, VirtualBox, VMWare Workstation Pro and Parallels with a total of 54 new bugs discovered and 6 CVEs assigned. If you're interested, read the paper, check out the source and reach out to us with any questions!
This work was a collaboration among Zheyu Ma, Qiang Liu, Zheming Li, Tingting Yin, Wende Tan, Chao Zhang, and Mathias Payer. Zheyu did the heavy lifting as a visiting PhD student at the HexHive laboratory and deserves the main credit for this work.