JavaScript engines face a dilemma: on one end, they need to be extremely efficient as they are processing millions of lines of JavaScript code, dynamically translating complex programs into efficient code. On the other end, the code may be controlled by an attacker that is trying to exploit bugs in the JavaScript engine to escalate their privileges on the user's computer. JavaScript engines must therefore balance performance and security.
Automated testing is a cornerstone to find and fix as many bugs in the JavaScript engine as possible but fuzzers are faced with the dilemma that complex bugs between different phases of the just-in-time compiler are hard to detect. JavaScript engines switch between different execution tiers, e.g., from a simple and inefficient but fast interpreter to highly optimized but slow compilation. Both the interpreter and the optimizing compiler must follow the same data and stack formats to allow seamless switching between tiers. Triggering --- and then detecting --- these bugs is challenging as information about this lower layer is not exposed to JavaScript where most existing fuzzers operate.
Our key idea is to instrument the JavaScript engine itself to record and dump detailed information whenever we switch execution profiles, allowing the fuzzer to compare states across engines. In Dumpling, we create a fuzzer that targets the different layers of the JavaScript engine and explores these state transition through detailed state dumping. Instead of only comparing single variables, we have a detailed overview of the exact execution and memory state. The key benefit is that these state comparison allows Dumpling to expose bugs before they are observable at the JavaScript layer.
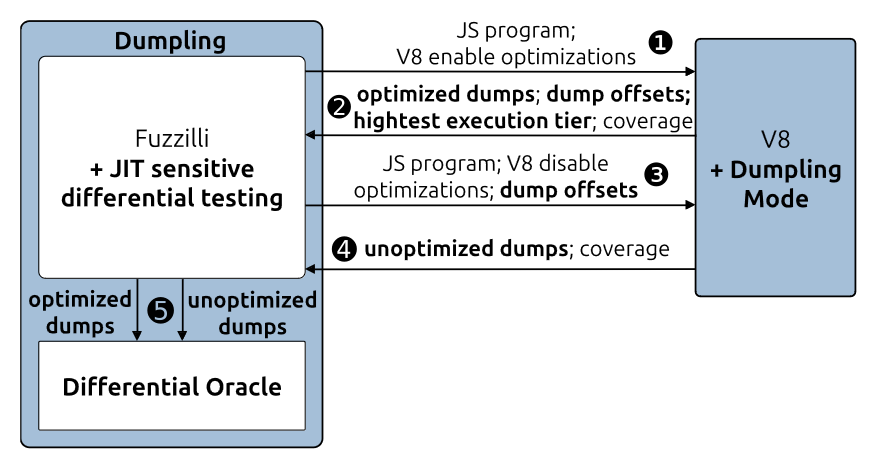
While the implementation is specific to V8, this JavaScript engine is used not just in Chrome but across many different projects. The hooks are lightweight and could be implemented in other engines with minimal engineering effort. In our evaluation, we showcase that the overhead is reasonable and the precision of our bug oracle enables the detection of eight severe bugs that we responsibly disclosed to Google.
The key takeaway of Dumpling is that by extracting some internal state and making it visible to the fuzzing engine, we have designed a bug oracle that is much more powerful than simply probing certain variables. Slight modifications of the underlying system may pay off in much higher precision!
This work was a collaboration among Liam Wachter, Julian Gremminger, Christian Wressnegger, Mathias Payer, and Flavio Toffalini. Liam and Julian deserve the majority of the credit for this project that they conducted during their master thesis at the HexHive. This work received all artifact evaluation badges and, at the conference, received a distinguished paper award.